Custom apps have become a significant part of businesses in this digital landscape. To achieve a competitive edge, businesses are inclining towards websites and applications, which also help in attracting customers. On the other hand, there is a consistent rise in remote work, requiring businesses to depend heavily on the cyber world.
However, the primary issue that is raised is cybersecurity.
Do you know that a cyberattack occurs around every 39 seconds?
It means that the prevalence of custom apps online exposes them to cyber threats. Security breaches can result in severe consequences like financial loss, reputational damage, and legal ramifications. Recent high-profile breaches highlight the imperative for strong cybersecurity measures to safeguard sensitive data and protect businesses from potential harm.
In today’s digital era, custom apps are vital assets for businesses. To safeguard these assets, it’s essential to integrate cybersecurity best practices into custom software development processes.
How does the custom app work?
A custom application, sometimes referred to as bespoke or tailor-made software, is a type of software solution created, developed, and implemented with a specific organization’s goals and specifications in mind. While pre-packaged software solutions cater to a wide range of users and offer generic capabilities, custom apps are designed to perfectly match the specific workflows, goals, and processes of a certain firm.
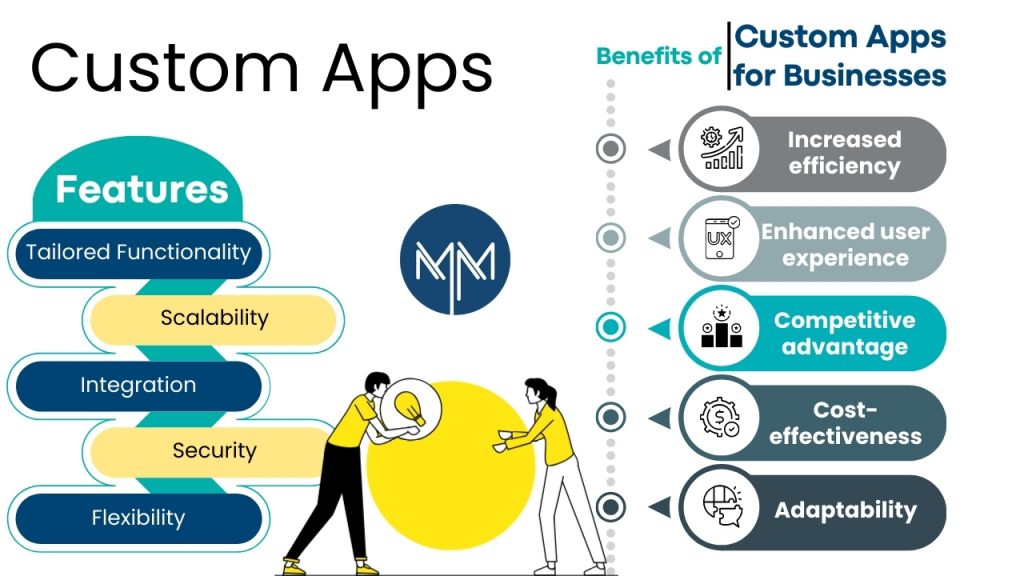
Let’s discuss some of the key features of custom apps:
- Tailored Functionality
- Scalability
- Integration
- Security
- Flexibility
Benefits of custom apps for businesses:
- Increased efficiency
- Enhanced user Experience
- Competitive advantage
- Cost-effectiveness
- Adaptability
By offering specialized solutions that address their unique demands and challenges, custom applications play a critical role in enabling organizations to achieve their goals and objectives.
Understanding the risks:
Custom applications offer businesses the flexibility and functionality they require to streamline operations and gain a competitive edge. However, these benefits come with inherent risks, particularly concerning security vulnerabilities.
Unlike off-the-shelf software, custom apps are often tailored to specific business processes, making them attractive targets for cybercriminals seeking to exploit weaknesses for financial gain or malicious intent.
Targeted Exploitation:
Custom applications are tailored to specific business processes, making them lucrative targets for cybercriminals. Attackers exploit weaknesses in custom apps to gain unauthorized access to sensitive data, intellectual property, or financial resources. The unique design and functionality of custom apps may provide attackers with opportunities to exploit vulnerabilities that are not present in off-the-shelf software.
Complexity and interconnectedness:
Custom applications often interact with other systems and databases within the organization’s IT infrastructure. The complexity of these interconnections increases the attack surface and the potential for security breaches. Attackers may target vulnerabilities in custom apps to gain access to interconnected systems or to launch broader attacks against the organization’s network.
Lack of security by Design:
Security is not always prioritized during the development of custom applications, leading to vulnerabilities that are inadvertently introduced into the software. Developers may focus more on functionality and meeting business requirements, neglecting essential security considerations. Without a security-first mindset, custom apps may contain flaws that can be exploited by attackers, posing significant risks to the organization.
Insider threats:
Insiders with access to custom applications pose a significant security risk, as they may abuse their privileges to exploit vulnerabilities or steal sensitive information. Malicious insiders, disgruntled employees, or contractors with access to custom apps can intentionally sabotage systems or misuse data for personal gain or malicious purposes. Insider threats highlight the importance of implementing robust access controls and monitoring mechanisms to detect and prevent unauthorized activities.
Lack of updates and maintenance:
Custom applications require regular updates and maintenance to address security vulnerabilities and mitigate emerging threats. However, organizations may neglect to prioritize updates due to resource constraints, leading to outdated software with known vulnerabilities. Attackers actively target unpatched custom apps, exploiting known vulnerabilities to compromise systems and exfiltrate data or disrupt operations.
Third-party dependencies:
Custom applications often rely on third-party libraries, frameworks, or components to expedite development or add functionality. However, these dependencies may introduce additional security risks if they contain vulnerabilities or are not properly vetted for security. Attackers can exploit weaknesses in third-party dependencies to compromise custom apps and gain unauthorized access to sensitive data or systems.

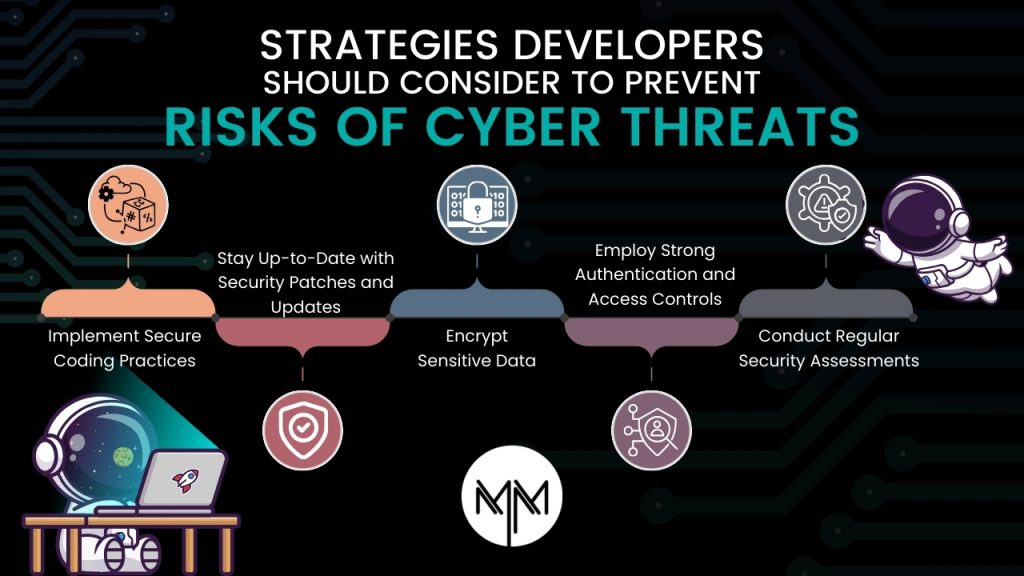
Strategies developers should consider to prevent risks
Cybersecurity in custom software development means putting strong defenses in place to make sure the program is safe from online threats. This involves implementing robust security measures, such as encryption, authentication, and access controls, to mitigate risks and protect sensitive data.
Let’s look into the strategies more specifically:
- Implement Secure Coding Practices: As a developer, you should follow secure coding standards to reduce common vulnerabilities like cross-site scripting (XSS) and injection attacks. These techniques include input validation, output encoding, and correct error handling. Through input sanitization and user data validation, developers can stop bad actors from taking advantage of holes in custom apps.
- Conduct Regular Security Assessments: Regular security assessments, including code reviews, penetration testing, and vulnerability scans, should be conducted throughout the development lifecycle to identify and remediate security flaws. By proactively identifying vulnerabilities and weaknesses, developers can strengthen the security posture of custom applications and mitigate the risk of exploitation by cybercriminals.
- Employ Strong Authentication and Access Controls: Strong authentication measures, such as multi-factor authentication (MFA) and secure password policies, can be put into place to help confirm user identities and limit access to only authorized individuals. To minimize the risk of unauthorized access to critical information or functionality, role-based access control, or RBAC, should be used to enforce granular permissions and limit privileges based on user roles and responsibilities.
- Encrypt Sensitive Data: Developers should prioritize data encryption both in transit and at rest to protect sensitive information from unauthorized access or interception. Utilizing robust encryption algorithms and secure protocols ensures the confidentiality and integrity of data, even if attackers manage to infiltrate the custom application or intercept communications.
- Stay Up-to-Date with Security Patches and Updates: Regularly updating and patching custom applications, as well as third-party dependencies, is essential to address known vulnerabilities and mitigate emerging threats. Developers should stay informed about security advisories and releases from vendors and promptly apply patches to eliminate security weaknesses that could be exploited by attackers. Additionally, automated patch management tools can streamline the process of deploying updates while minimizing downtime and disruption to operations.
Key Takeaways:
- Custom applications offer businesses tailored solutions but are susceptible to cyber threats due to their unique design.
- Developers must prioritize security throughout the development lifecycle, implementing secure coding practices and regular assessments.
- Strong authentication, access controls, and data encryption are crucial for safeguarding sensitive information.
- Staying up-to-date with security patches and updates is essential to address vulnerabilities and mitigate emerging threats.
- Collaboration across teams and ongoing education are vital for fostering a culture of security awareness and accountability within organizations.
Conclusion
Robust security measures are more important than ever as businesses continue towards digital transformation and depend on custom applications to fuel development and innovation. Organizations can create custom applications that are resistant to new cyber threats and protect sensitive data from unauthorized access and exploitation by incorporating security into every stage of the development lifecycle and following best practices and principles of secure app development.
Furthermore, in the era of expanding cyber threats, encouraging teamwork and education guarantees that security stays a primary concern and a continuous commitment.
Consult with Matrix Media Solutions for expert guidance in developing a secure custom app tailored to your business needs. With our expertise, we ensure the strongest possible application, fostering a secure digital future for individuals and companies alike. Let’s collaborate for enhanced security!


 January 24, 2024
January 24, 2024